- info@cyforce.in
- +91-9702823777
- +91-9821256993
- Mon - Sat: 10:00 AM - 6:00 PM
Network Penetration Testing
Network Penetration Testing
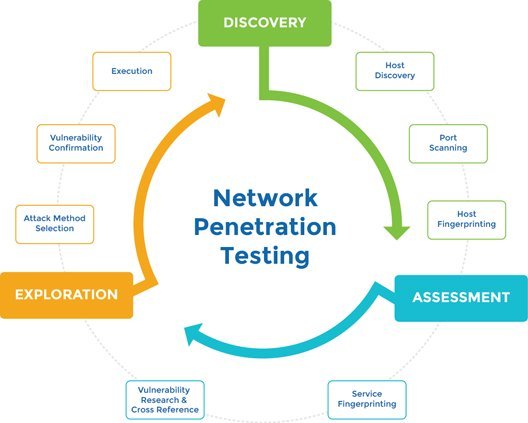
1. Introduction to Network Penetration Testing:
• What is network penetration testing ?
Network penetration testing, also known as ethical hacking, is a methodical approach to evaluating the security of a computer network. It involves simulating real-world cyber attacks to identify vulnerabilities and assess the overall resilience of the network.
• Why is it important for businesses?
Businesses today face increasing cybersecurity threats, and network penetration testing helps identify weaknesses before malicious actors can exploit them. It allows organizations to proactively strengthen their security measures, protect sensitive data, and maintain the trust of their customers.
• Benefits of conducting network penetration tests
Network penetration testing, also known as ethical hacking, is a methodical approach to evaluating the security of a computer network. It involves simulating real-world cyber attacks to identify vulnerabilities and assess the overall resilience of the network.
a) Identify vulnerabilities: Uncover weaknesses in network infrastructure, systems, and applications.
b) Risk mitigation: Prioritize and address vulnerabilities to minimize potential risks.
c) Compliance requirements: Meet industry-specific regulatory compliance standards.
d) Enhanced incident response: Develop effective response plans based on realistic attack scenarios.
2. Types of Network Penetration Testing:
a) External penetration testing:
• Uncover weaknesses in network infrastructure, systems, and applications.
• Identifying potential entry points for attackers.
• Evaluating firewall effectiveness and network segmentation.
b) Internal penetration testing:
• Evaluating vulnerabilities within the internal network.
• Assessing user access controls, privileges, and permissions.
• Testing for lateral movement and escalation of privileges.
c) Wireless network penetration testing:
• Assessing the security of wireless networks, including Wi-Fi and Bluetooth.
• Identifying weak encryption, unauthorized access points, and rogue devices.
• Evaluating wireless network isolation and authentication mechanisms.
3. Common Network Vulnerabilities:
a) Weak or default passwords:
• Assessing the strength of passwords used across the network.
• Identifying accounts with default or easily guessable passwords.
• Recommending stronger password policies and multi-factor authentication.
b) Unpatched software and outdated systems:
• Identifying missing security patches and outdated software versions.
• Assessing the impact of unpatched vulnerabilities on network security.
• Providing recommendations for regular patch management and updates.
c) Wireless network penetration testing:
• Assessing the security of wireless networks, including Wi-Fi and Bluetooth.
• Identifying weak encryption, unauthorized access points, and rogue devices.
• Evaluating wireless network isolation and authentication mechanisms.
d) Social engineering attacks:
• Testing the organization's susceptibility to phishing, vishing, or physical attacks.
• Raising awareness among employees about social engineering tactics.
• Implementing security awareness training and incident response plans.
4. Methodologies and Tools:
a) Overview of penetration testing methodologies:
• Explanation of the steps involved in a typical penetration testing engagement.
• Introduction to methodologies like the Open Web Application Security Project (OWASP) Testing Guide and Penetration Testing Execution Standard (PTES).
• Recommending stronger password policies and multi-factor authentication.
b) Popular penetration testing tools:
• Brief descriptions and use cases for widely used tools like Nmap, Metasploit, Burp Suite, Wireshark, and more.
• Explaining how these tools aid in vulnerability scanning, exploitation, and post-exploitation activities.